Circuits
We split OpenPassport circuits into two steps according to a Semaphore-style design. This lets users do actions without revealing which signature algorithm was used to sign their passport.
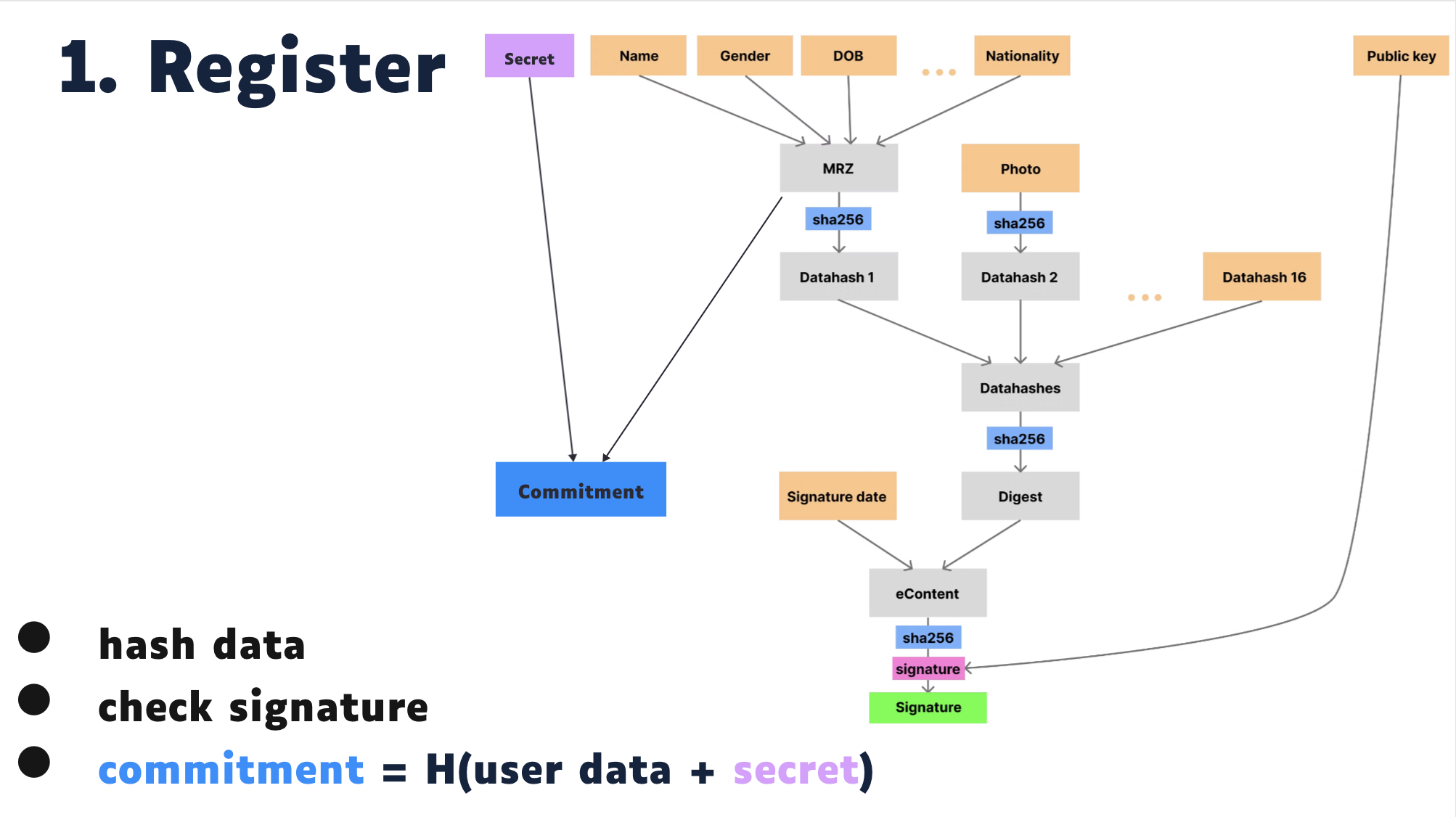
The first step is registration. It allows users to prove their passport is valid without revealing any of their private data.
We currently support two signature algorithms:
sha1WithRSAEncryption
We are working on adding more, see details here.
After the proof is generated, it is sent to a smart contract and adds a commitment to a merkle tree. The tree is currently on Optimism, but can be migrated easily. The hash of the issuer's signature is used as a nullifier.
The second step is interaction, also called broadcasting a message in Semaphore.
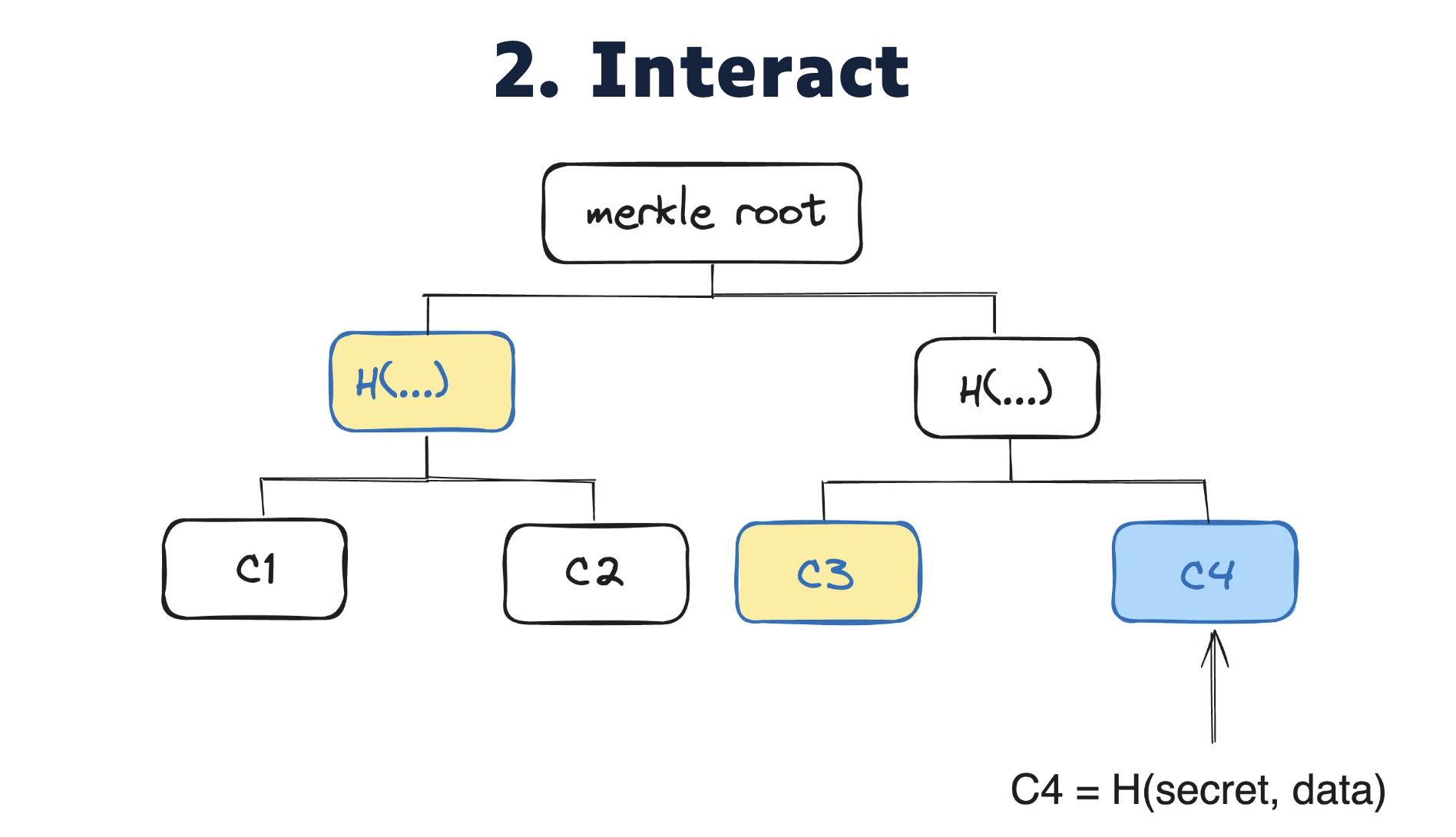
It involves proving inclusion of the commitment in the merkle tree, and optionally disclosing some private data. Any data in the MRZ can be disclosed thanks to a bitmap passed as private inputs. This includes:
Issuing state
Name
Passport number
Nationality
Date of birth
Gender
Expiry date
Additionally, we crafted specific modules in the circuit to disclose:
Passport is not expired
Age is above a certain threshold
A user_identifier is committed in this proof. For onchain usage, it is used to avoid frontrunning. For offchain usage, it can be used by apps to identify users uniquely and make sure someone who obtains a proof later cannot impersonate someone.
Last updated